Phishing
This blog provides detailed information on phishing and aims to educate readers and raise awareness as well as offers a comprehensive guide and practical tips to stay safe in our day-to-day life.
Phishing - one of the most common online scams/frauds: what it is, how it works, examples, risk, detection, prevention with report to whom and how also find images for your reference.
What is Phishing?
Phishing is a type of social engineering attack where scammers pretend to be a trusted entity like bank, service provider, government, etc., to trick people into revealing sensitive information - like passwords, credit card numbers, bank account details, etc.
These messages can come via email, SMS (“smishing”), phone calls (“vishing”), or sometimes via fake websites, apps, links.
How It Works? A Typical Phishing Workflow
1. Target Identification
The scammer picks a target broadly or specifically (General or exact). Sometimes it's a random person, sometimes a business or high-value individual.
2. Crafting the Bait (Target Individual)
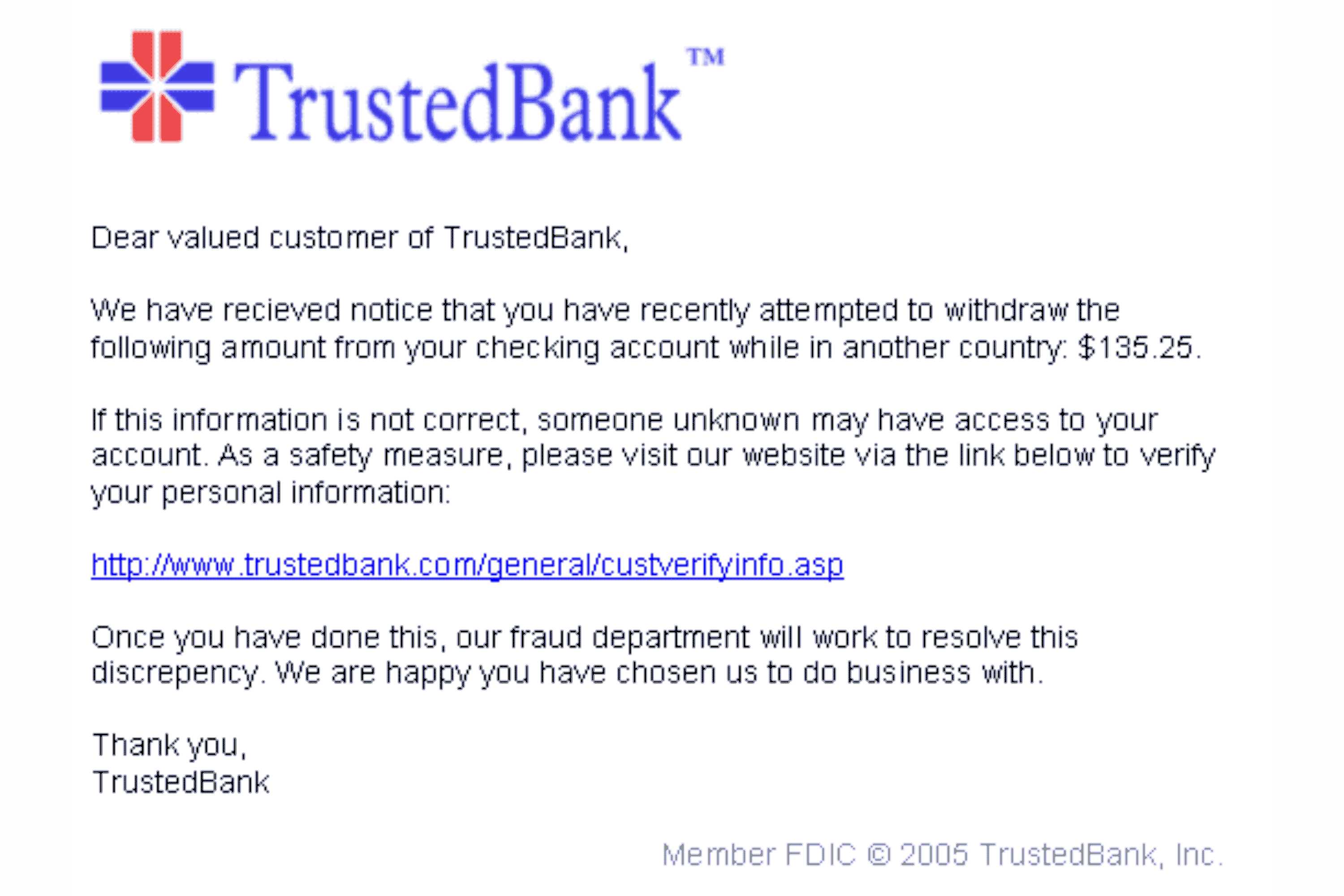
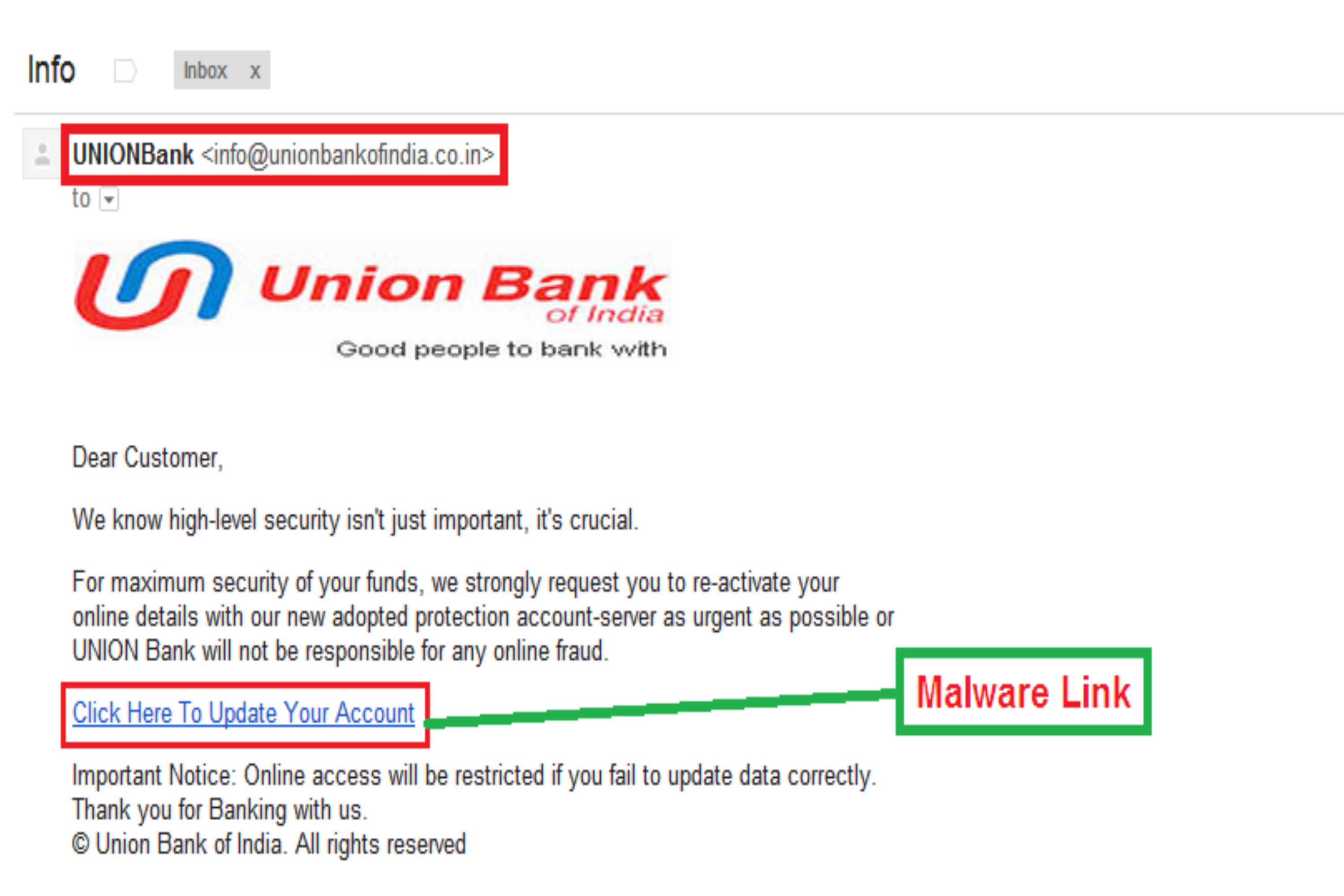
They create a message (email, SMS, link etc.) that looks genuine. It often uses official logos, names, familiar branding, or impersonates a trusted service. They may also use urgency (“Your account will be blocked,” “Payment failed,” “Unusual activity noticed,” etc.) to emotionally push the victim to respond quickly.
3. Delivery
The message is sent. The message often includes a link to a fake website, or an attachment, or sometimes a request to call a phone number.
4. Harvesting Information / Exploitation
If the victim clicks a link, they may be led to a site looking just like the real one, entering login credentials, OTPs, banking/personal information, etc. Sometimes malware or spyware is downloaded. The fraudster uses the information to steal money, identity theft, or further exploit the victim.
Types of Phishing / Modern Trends
- Smishing: phishing via SMS/text messages.
- Vishing: using voice calls.
- Spear phishing: highly targeted phishing (to specific individuals or organizations), often using personalized data.
- AI-powered phishing: using generative AI to write more convincing messages, less detectable by usual pattern-based filters.
- Quishing: phishing using QR codes (fake QR codes).
Some Examples
- A common example: an email appears from your bank saying “we detected unusual activity, click here to verify,” link leads to a fake login page.
- In India: fake SMS or WhatsApp messages pretending to be from your bank about account issues or needing to update documents, with a link to download a malicious app (APK) or site to enter your bank details.
What are Major Risks or its Consequences
- Loss of money from bank accounts or credit cards even you can be a victim of monthly EMI.
- Identity theft (misuse of your identity, opening accounts in your name, can apply for loans).
- Access to your email, social media, or other accounts.
- Malware infection, ransomware, etc.
- Stoles personal data and can asks for money to retrieve data
How to Recognize Phishing?
Some warning signs (Red flags):
- Unsolicited messages or calls — especially asking for urgent action.
- Generic greetings (“Dear Customer”) instead of your real name.
- Slight spelling or grammar mistakes.
- Fake or spoofed email addresses or URLs that resemble the real ones (but differ slightly). For example, “bank‑secure.com” instead of “bank.com.”
- Links that don’t match what they claim; hovering shows different address. Always has a different website than the official website just has slight matching name.
- Look for official website. whether its original website or not.
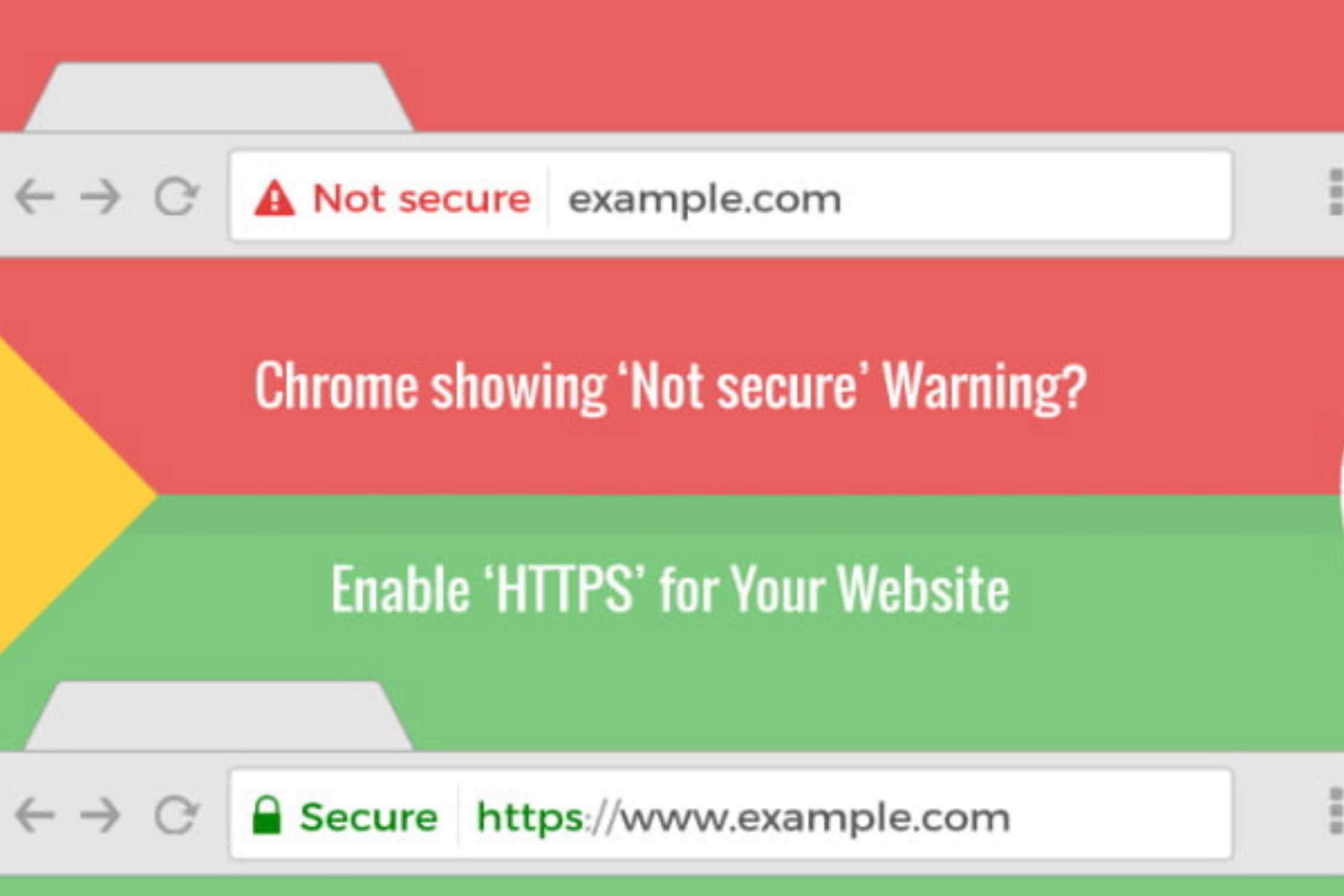
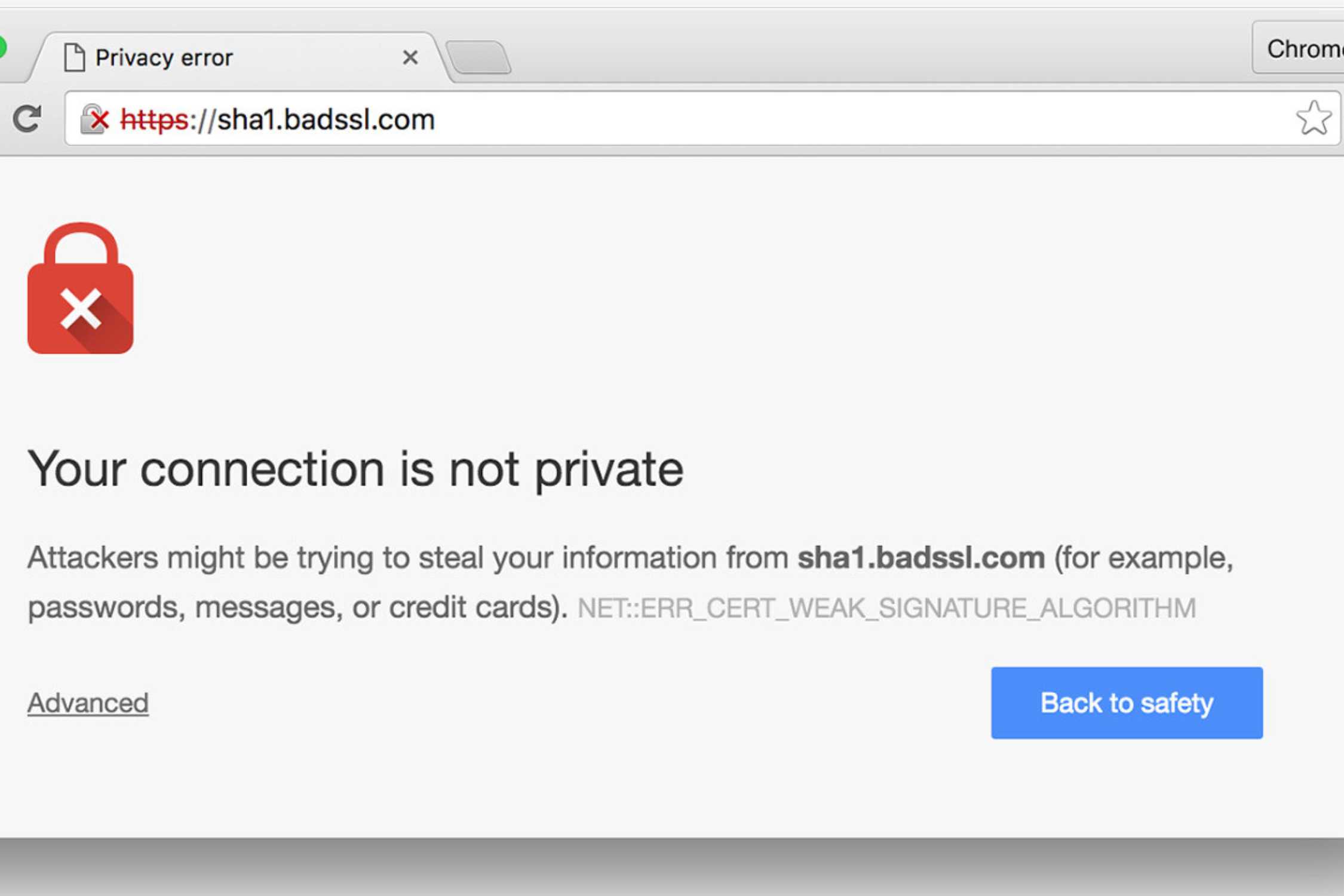
- Secure‑site indicators missing or questionable (no HTTPS, no lock icon). Websites with no Http or Https, these sites are unsecured sites. If you have antivirus installed then it will block automatically or prompt you to proceed, but if you don’t have antivirus installed then it will proceed or prompt you by windows default security system (In case you have kept it enable), but when page loads it will show “unsecured connection” on left side of address bar (image is attached in page slider for your reference).
- Asking for passwords, OTP, or financial info through email or unsolicited methods. Legit organizations typically don’t ask this way. Here we have to remember Bank or any Genuine Institution never asks for Password, OTP, or any other confidential or personal data.
Prevention & What should you do
- Never click on suspicious links or attachments.
- If in doubt, go to the official site directly (type URL manually) or call the official customer care.
- Use two‑factor/multi‑factor authentication (2FA) where possible.
- Keep software / antivirus / browser up to date.
- Use email spam filters and phishing protection tools.
- Don’t enter personal information just because someone claims there's a problem. Always verify first.
- Educate and create awareness - even among family and friends.
What To Do If You Think You’ve Been Phished
- Change passwords immediately.
- Contact the bank or organization involved.
- Monitor your accounts for unauthorized transactions.
- Consider placing fraud alert if identity theft is possible.
Report the incident to relevant authorities or cybercrime units. Go to https://cybercrime.gov.in and follow the steps that apply to the type of scam victim you are.
Related Videos
No videos available for this post.


No comments yet. Be the first to comment!